Welcome to our Crypto Insider for March 23rd, 2022 – FREE Edition.
By popular demand, we’re bringing you the smartest insight, analysis, and investing tips for all things Crypto.
Today, we’ll be going over some common hacks and dangers to be aware of, and the things you can do to better protect your cryptocurrency. Forewarned is forearmed, and all that.
Let’s go!
Table of Contents
How to Manage Your Cryptocurrency Safely
Why the bad rap?
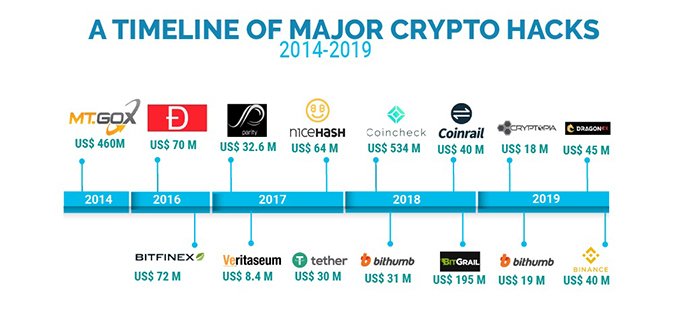
It’s no secret that cryptocurrency has gotten a bad rap, and a big part of it is the many hacks and compromises that have happened involving various coins.
One of the most recent and public ones involves the fast-rising crypto.com, which now owns the naming rights of the previously known Staples Center, in which $34M worth of crypto was taken.

Some dangers of Cryptocurrency
Cryptocurrency can get hacked in dozens of other ways, but below are the three most common risks that result in users getting their money stolen. And you definitely need to know about them.
1. Smart Contract Exploits
We’ve talked about smart contracts before and how they are at risk of being exploited, even if they are audited by 3rd party security farms. For each decentralized app (dapp), you engage with your digital wallet (such as Meta Mask) enter a smart contract.
Let’s say you are taking advantage of some juicy defi yields on platforms like Popsicle Finance by putting $5,000 worth of $ETH and $USDC into a liquidity pool for a juicy 40%+ APR.
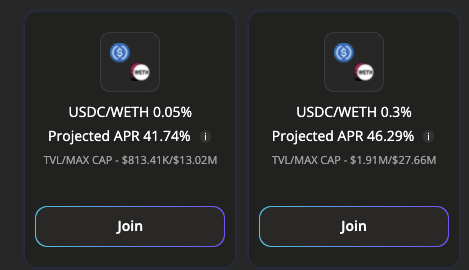
Participating in the liquidity pool means you’re using a smart contract in which Popsicle Finance holds onto the aforementioned $ETH and $USDC. If a hacker finds a bug and hacks the smart contract, they may be able to steal the part of or all of your $ETH and $USDC that Popsicle Finance has.
How to mitigate smart contract exploit risks
- Only engage with dapps that 3rd party companies like Certik have audited
- Find older, most established projects that have a high total value locked (TVL)
- Research the team behind the dapp to ensure its a trustworthy team
- Follow the project on Twitter and join the project’s discord. When hacks happen, projects will usually let their users know what they can do to secure their assets
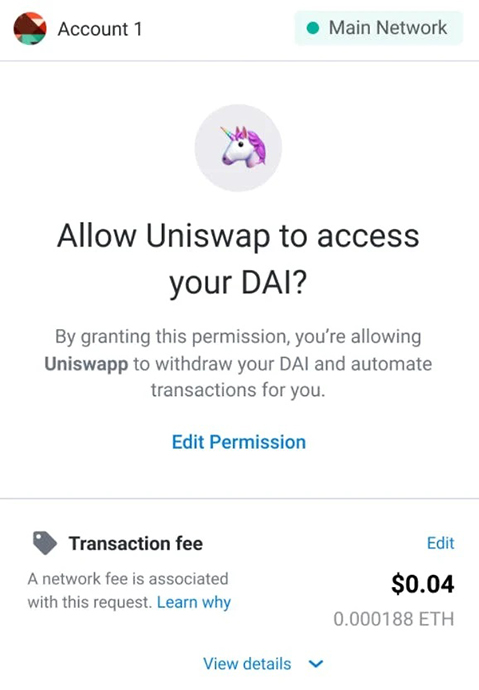
2. Accidental Permission
To engage with a dapp and a smart contract, you need to opt-in to requests by granting permission. While this is not a big risk with trustworthy dapps, there are plenty of dapps that want to take your cryptocurrency.
Many people don’t fully read what they are agreeing to when they grant permission for dapps to interact with their digital wallet. These malicious dapps can sneakily:
- Ask for assets that are unrelated to the intended transaction
For example, let’s say the dapp through your browser says it wants to access your $ETH, but in the actual request, it requests access to $ETH, $USDC, and $MIM. If you say yes, all 3 assets are at risk as the $dapp now has your permission to engage with all 3 cryptocurrencies.
- Drain your wallet by asking for permission for more of an asset than you expect
An example of this is if the dapp through the browser says it will take .1 $ETH, but it actually asks for 10 $ETH in the request. This is quite common, actually, as many people skim over the numbers.
How to mitigate accidental permission risk:
- Engage with trustworthy dapps
- Read every request carefully to make sure you know what you are granting permission to
- If you’re not sure, ask around in the discord about the language you are confused or uncertain about
3. Computer Exploits, Viruses & Malware
While this one is actually not unique to cryptocurrency, it is common enough for us to mention it. Viruses can log everything that happens to your computer, including your cryptocurrency transactions.
If your computer is hacked or has a virus, the hackers may be able to drain your cryptocurrency assets.
How to mitigate computer exploits, viruses, & malware:
- Be wary of the sites you visit, as they can put viruses or malware on your computer
- Be wary of anything you download, as downloaded files can also lead to exploits
Different Ways to Store Your Cryptocurrency
There are a number of ways to store cryptocurrency, each with varying levels of convenience and safety.
Centralized Exchanges
A centralized exchange (CEX) is an application where you can buy cryptocurrency with fiats such as Coinbase and the Crypto.com mentioned before.
Many cryptocurrency holders hold at least some of their cryptocurrency on centralized exchanges, and most beginners hold all of their cryptocurrency assets on CEXs. Holding your crypto on a CEX is considered the least secure method of the 3 we discuss here, as a CEX can be hacked, and your account on the CEX can be compromised.

While CEXs will likely reimburse you to protect their reputation, there is no guarantee they will. It’ll be an annoying headache to figure out how and when you will be reimbursed even if they do.
If you are holding your assets at a CEX, you are not engaging in any smart contracts, so you don’t have to worry about the first 2 risks we mentioned in the previous section.
Digital Wallets
Digital wallets are online wallets that hold your cryptocurrency. If you follow proper wallet management, digital wallets are more secure than CEXs.
The most popular is MetaMask, which is a digital wallet for Ethereum and ERC-20 tokens. However, you may need different digital wallets for different coins and chains, such as Phantom for Solana ($SOL).
Digital wallets are more secure than CEXs if you take good care of your passwords and seed phrases, a unique set of words used to grant permission to digital wallets, similar to a password. However, seed phrases can’t be changed. Ever.
Using Multiple Digital Wallets
Let’s say you have 2 $ETH, 1,500 $USDC, and 5,000 $MIM, and you want to take advantage of defi with a dapp called BADDIE, which involves staking your 1,500 $USDC.
Let’s also say you have a MetaMask wallet which we’ll call WalletA.
If you use WalletA to engage with BADDIE, you could be risking all of your assets… But you don’t have to.
This is where having multiple digital wallets can be helpful. You create a second wallet, WalletB, and send the $USDC to WalletB. Then you use WalletB to interact with BADDIE.
This way, you never grant BADDIE permission to WalletA, which holds your 2 $ETH and 5,000 $MIM. Because only WalletB interacted with BADDIE, it’s just the 1500 $USDC that is at risk.
You can create as many wallets as you need to as well, and the more you have, the more secure your assets will be.

Hardware Wallets
Hardware wallets are physical devices that let you hold and manage multiple coins. The two leading companies are Trezor and Ledger. Hardware wallets are the safest of the 3 ways to secure your cryptocurrency.
They help secure your cryptocurrency assets by requiring the physical wallet to be connected to the computer in order to interact with your cryptocurrency. As long as you have the physical device, you can log in and access your wallet anywhere.
Like with digital wallets, hardware wallets let you create multiple wallets to store your cryptocurrency. This allows you to still follow best practices to never have your primary wallet connected to dapps and just use intermediary wallets, like walletB in the example we provided in the previous section.
This way, it makes it much more difficult to steal cryptocurrency from hardware wallets because the physical device is needed, making it almost impossible for overseas bad actors to interact with your wallet.
However, in cases where your computer has a virus or malware, your hardware wallet can still be compromised.
Wrapping Up
It’s not hard to keep your cryptocurrency secure. It just requires some common sense, research, and not being lazy. If you follow the tips laid out here, you should be able to avoid the most common risks of cryptocurrency.
Definitely consider getting a hardware wallet to lock down your cryptocurrency and minimize the chances of getting your wallets drained. And remember – if something is too good to be true, then it probably is.
Many dapps are bad actors with malicious intent – always do your own research.